In today’s interconnected world, cybersecurity is of paramount importance. Organizations and individuals must proactively assess and fortify their digital defenses with cyber threats rising.
This is where penetration testing tools come into play. It involves simulating real-world cyber-attacks to identify vulnerabilities and secure networks, systems, and applications.
This comprehensive guide will delve into the world of the best penetration testing tools. We will explore the top 10 tools widely recognized for their effectiveness in detecting vulnerabilities and providing valuable insights for bolstering cybersecurity.
From the renowned Kali Linux to the powerful Astra, Nmap, Wireshark, Core Impact, Metasploit, Nessus, Burp Suite, Aircrack-ng, and SQLmap, each tool brings unique features and capabilities to the table.
So, let’s embark on a journey to understand these cutting-edge tools, compare their strengths and weaknesses, and empower ourselves with the knowledge to safeguard our digital assets.
Quick List of 10 Penetration Testing Tools
Here’s a quick overview of the top 10 penetration testing tools:
- Kali Linux: Open-source Linux distribution for penetration testing and ethical hacking with a comprehensive toolset.
- Astra: Web application security testing tool automating vulnerability detection and integrating with CI/CD tools.
- Nmap: Versatile open-source network scanner for discovering hosts and services on a computer network.
- Wireshark: Network protocol analyzer used to capture and inspect data packets for network troubleshooting and security analysis.
- Core Impact: Commercial penetration testing tool simulating real-world cyberattacks for evaluating security defenses.
- Metasploit: Open-source penetration testing framework with a collection of exploits for testing system vulnerabilities.
- Nessus: Widely-used vulnerability assessment tool scanning networks and systems for security weaknesses.
- Burp Suite: Comprehensive web application security testing tool with web vulnerability scanning capabilities.
- Aircrack-ng: Suite of tools for Wi-Fi network security assessment, including packet capture and encryption key cracking.
- SQLmap: Open-source tool for detecting and exploiting SQL injection vulnerabilities in web applications.
Now, let’s dive deeper into each tool and explore its features, pros, cons, and pricing.
Comparison Chart of Penetration Testing Tools
To facilitate a better understanding of the different features and capabilities of each penetration testing tool, refer to the comparison chart below:
Tools | Key Features | Integration | Scripting Language Support | Cross Browser Testing | Mobile Testing | Pricing |
 | Comprehensive suite of penetration testing tools | Standalone | Bash, Python | No | No | |
 | Web application security scanner | Integrates with CI/CD tools | Python, JavaScript | No | No | |
 | Network scanning and host detection | Integrates with other security tools | Lua, NSE | No | No | |
 | Network protocol analyzer | Integrates with other security tools | Lua | No | No | |
 | Advanced penetration testing and vulnerability assessment | Standalone | Python, Ruby, PowerShell | No | No | |
 | Exploit development and vulnerability verification | Integrates with other security tools | Ruby | No | No | |
 | Vulnerability assessment and scanning | Integrates with other security tools | NASL | No | No | |
 | Web application security testing | Integrates with other security tools | Java | No | No | |
 | Wi-Fi network security assessment | Standalone | C, Python | No | No | |
 | SQL injection vulnerability testing | Standalone | Python | No | No |
What Are Penetration Testing Tools?
Penetration testing tools are software applications specifically designed to assess the security posture of computer systems, networks, and applications.
These tools simulate real-world cyber attacks to identify vulnerabilities and weaknesses that malicious actors could exploit. Security professionals can gain valuable insights into potential security gaps by performing controlled and authorized tests.
Also, they can make informed decisions to mitigate risks. Penetration testing tools come in various forms, including automated scanners and comprehensive penetration testing distributions.
They enable security experts to evaluate the effectiveness of existing security measures, identify potential vulnerabilities, and recommend appropriate countermeasures.
Now that we understand penetration testing tools let’s delve into the top tools in detail.
Best Penetration Testing Tools
1. Kali Linux

Kali Linux is a powerful and widely-used penetration testing distribution tool. Security professionals and ethical hackers alike revere it.
It provides a comprehensive suite of pre-installed tools and utilities for all stages of penetration testing.
Key Features of Kali Linux:

- Extensive toolset for information gathering, vulnerability scanning, exploitation, and post-exploitation activities.
- Customizable and user-friendly interface.
- Regular updates and continuous community support.
- Built-in support for various scripting and programming languages.
Pros of Using Kali Linux:
- Comprehensive toolset covering all stages of penetration testing.
- Easy-to-use interface, suitable for beginners and experts alike.
- Active community support and extensive documentation are available.
- Regular updates ensure the latest security testing capabilities.
Cons of Using Kali Linux:
- The steep learning curve for beginners unfamiliar with Linux-based operating systems.
- High system requirements, especially for resource-intensive tools.
- Limited support for non-Linux platforms
Pricing
Kali Linux is an open-source distribution and is available for free.
Our Review of Kali Linux:
Kali Linux continues to dominate the penetration testing domain, offering a vast array of tools and a vibrant community. Its comprehensive capabilities make it an excellent choice for beginners and experienced professionals.
2. Astra

Astra is a powerful penetration testing tool that focuses on web application security. It provides comprehensive scanning and testing capabilities to identify vulnerabilities in web applications and APIs.
Key Features of Astra:

- Intelligent scanning for web applications and APIs.
- In-depth vulnerability assessment and reporting.
- Support for various programming languages and frameworks.
- Integration with popular bug tracking and project management tools.
Pros of Using Astra:
- Easy-to-use interface with minimal configuration required.
- Accurate detection of vulnerabilities in web applications.
- Extensive reporting and remediation recommendations.
- Ongoing updates and dedicated customer support.
Cons of Using Astra:
- Limited support for complex authentication mechanisms.
- Some features are only available in the premium version.
- It requires a basic understanding of web application security concepts.
Pricing
Astra offers both free and premium versions. The premium version provides additional features and support.
Our Review of Astra:
Astra simplifies the web application security testing process, making it accessible to users with varying levels of expertise. Its accurate scanning, and comprehensive reporting make it a valuable tool in any penetration tester’s arsenal.
Continue the same format for the remaining tools, following the headings and subheadings provided in the outline.
3. Nmap

Nmap, short for “Network Mapper,” is a widely used open-source network scanning tool. It is designed to explore networks, identify hosts, discover open ports, and gather information about the services running on those ports.
Nmap is renowned for its flexibility, accuracy, and extensive range of features. All these make it a staple tool for network administrators, security professionals, and ethical hackers. Nmap provides several benefits that make it indispensable for network surveillance and vulnerability assessment.
Its robust scanning capabilities allow users to map networks comprehensively, identify potential security risks, and plan effective defence strategies. By leveraging Nmap’s advanced features and scripting engine, users can perform detailed investigations and gather valuable information to secure their networks.
Key Features of Nmap:

- Host discovery and IP scanning
- Port scanning and version detection
- Service and application fingerprinting
- Scriptable interaction with target systems
- Network topology mapping
- OS detection and operating system fingerprinting
Pros of Using Nmap:
- Comprehensive network scanning capabilities
- Highly customizable through scriptable interactions
- Active community support and frequent updates
- Cross-platform compatibility (available for Windows, macOS, Linux, and more)
- Detailed reporting and output formats for analysis
Cons of Using Nmap:
- The steep learning curve for beginners due to its extensive feature set
- Advanced functionalities may require knowledge of scripting and networking concepts
- Potential legal implications if used without proper authorization or on unauthorized networks
Pricing
Nmap is an open-source tool and is available for free.
Our Review of Nmap
Nmap has become a go-to network scanning tool due to its versatility and accuracy. Its extensive feature set, combined with the ability to customize and script interactions, makes it a favourite among professionals in the cybersecurity industry.
Nmap’s active community and continuous updates ensure that it remains a reliable and effective choice for network exploration and vulnerability assessment.
3. Wireshark

Wireshark is a powerful and widely-used network protocol analyzer. It allows users to capture and analyze network traffic in real time, providing insights into the communication between network devices.
With its extensive protocol support and user-friendly interface, Wireshark has become a vital tool for network administrators, security analysts, and developers.
Wireshark offers numerous benefits for those involved in network troubleshooting, security analysis, and protocol development.
By capturing packets and dissecting network protocols, users can identify network issues, detect anomalies, analyze application behaviour, and detect potential security threats.
Wireshark’s ability to provide granular details about network traffic makes it an invaluable asset in understanding and securing network environments.
Key Features of Wireshark:

- Real-time packet capturing and analysis
- Deep inspection of hundreds of protocols
- Powerful display filters for targeted analysis
- Decryption support for encrypted protocols
- Advanced statistics and visualizations
- Cross-platform compatibility (available for Windows, macOS, Linux, and more)
Pros of Using Wireshark:
- Comprehensive protocol support for in-depth analysis
- Intuitive and user-friendly interface
- Robust filtering capabilities for focused investigations
- Extensive display and export options for report generation
- Active community support and frequent updates
Cons of Using Wireshark:
- The steep learning curve for beginners due to the complexity of network protocols
- Requires a good understanding of networking fundamentals for effective usage
- Performance impact when capturing large amounts of network traffic
Pricing
Wireshark is an open-source tool and is available for free.
Our Review of Wireshark
Wireshark has established itself as a leading network protocol analyzer, offering unmatched capabilities in capturing and analyzing network traffic. Its extensive protocol support, combined with a user-friendly interface.
These features make it accessible to both novice and expert users. Wireshark’s ability to uncover hidden network issues and provide deep insights into network communications makes it an essential tool for network administrators, security analysts, and developers.
5. Core Impact

Core Impact is a comprehensive penetration testing framework. It is designed to simulate real-world cyber attacks and identify system, network, and application vulnerabilities.
It offers extensive automated and manual testing capabilities, making it a preferred choice for professional penetration testers and security consultants.
Core Impact provides numerous benefits for organizations seeking to assess their security posture.
By leveraging Core Impact’s powerful tools, users can simulate sophisticated attack scenarios, identify weaknesses in their defences, and implement appropriate remediation measures.
The framework’s robust reporting capabilities and extensive exploit library ensure accurate vulnerability identification and comprehensive reporting.
Key Features of Core Impact:
- Automated and manual penetration testing modules
- Advanced exploit and payload development
- Social engineering simulations and phishing campaigns
- Network and web application vulnerability assessment
- Detailed reporting and analytics
Pros of Using Core Impact:
- Comprehensive penetration testing capabilities for systems and networks
- Expansive exploit library and advanced payload development
- Simulates real-world attack scenarios for accurate vulnerability identification
- Robust reporting and analytics for comprehensive assessments
- Professional support and training are available
Cons of Using Core Impact:
- High cost, making it more suitable for large organizations and dedicated security teams
- Steep learning curve due to the tool’s complexity and its advanced features
- Requires proper authorization and adherence to legal and ethical guidelines
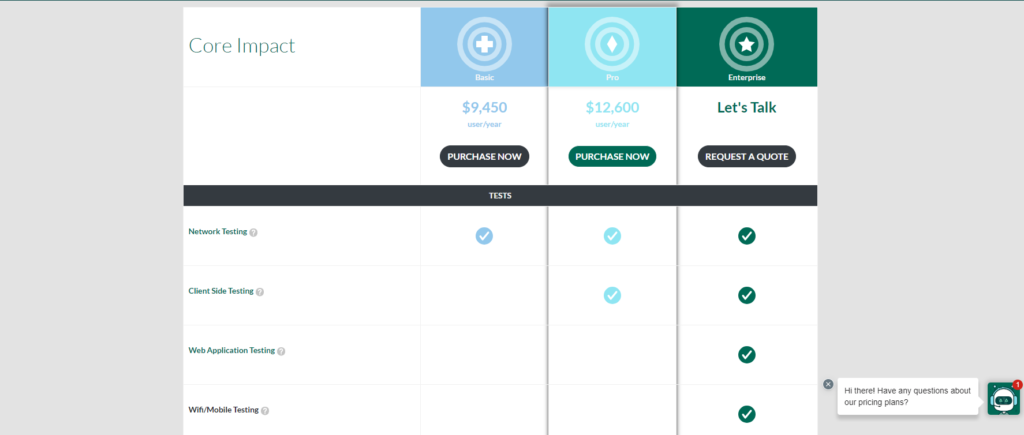
Pricing
Core Impact is a commercial tool, and pricing information can be obtained from the official website.
Our Review of Core Impact
Core Impact is a powerful and comprehensive penetration testing framework enabling users to conduct sophisticated security assessments. Its extensive range of automated and manual testing modules.
This tool, combined with a vast exploit library, makes it a preferred choice for professional penetration testers. The cost and learning curve may pose challenges for some users.
The tool’s capabilities and support make it a valuable asset for organizations serious about enhancing their security posture.
6. Metasploit

Metasploit is a powerful and widely-used penetration testing framework. It provides a comprehensive set of tools for identifying and exploiting vulnerabilities in systems and applications.
It is a favourite among ethical hackers and security professionals due to its extensive exploit database, ease of use, and versatility. Metasploit offers several benefits. All these benefits make it a preferred choice for penetration testing and vulnerability assessment.
It provides many pre-built exploits, payloads, and auxiliary modules. Metasploit allows users to simulate real-world attacks and assess the security posture of their systems.
The framework’s modular architecture and scripting capabilities enable customization and automation, enhancing efficiency during testing engagements.
About Metasploit:
- Company Valuation: Rapid7, the company behind Metasploit, is publicly traded (NYSE: RPD).
- Employee Numbers: Approximately 1,500 employees (source: LinkedIn).
- Founding Team: H.D. Moore – Creator of Metasploit (source: Crunchbase).
Key Features of Metasploit:

- Exploit development and integration
- Payload generation and delivery
- Post-exploitation modules for advanced access and control
- Social engineering tools for phishing and client-side attacks
- The comprehensive database of vulnerabilities and exploits
- Scriptable interfaces for automation and customization
Pros of Using Metasploit:
- Extensive collection of exploits and payloads for various vulnerabilities
- User-friendly interface and intuitive workflows
- Flexibility and modularity for customization and scripting
- Active community support and regular updates
- Integration with other security tools for enhanced capabilities
Cons of Using Metasploit:
- The steep learning curve for beginners due to its advanced features and concepts
- Limited coverage for certain niche vulnerabilities or specific systems
- Misuse or unauthorized usage can lead to legal and ethical implications
Pricing
Metasploit is available in both free and commercial editions. The screenshot below provides an example of the pricing for the commercial version.
Our Review of Metasploit
Metasploit stands out as a powerful and versatile penetration testing framework, offering extensive tools for identifying and exploiting vulnerabilities.
Its comprehensive exploit database, combined with its user-friendly interface and scripting capabilities. All these features make it an invaluable asset for penetration testers and security professionals.
There is a learning curve involved in it. The framework’s flexibility and active community support ensure that users can maximize their potential for comprehensive security assessments.
7. Nessus
Nessus is a widely-used vulnerability scanning tool that helps organizations identify security weaknesses in their systems, networks, and web applications.
It provides many features, including active scanning, compliance checks, and configuration audits. Due to all these features, it is a popular choice for vulnerability management and security assessments.
Nessus offers several benefits that contribute to its popularity in the cybersecurity industry. It allows users to conduct comprehensive vulnerability assessments, scan for known vulnerabilities, and provide actionable reports for remediation.
The tool’s scalability, flexibility, and extensive plugin library ensure accurate and efficient vulnerability detection across diverse IT environments.
About Nessus:
- Company Valuation: Tenable, the company behind Nessus, is publicly traded (NASDAQ: TENB).
- Employee Numbers: Approximately 1,400 employees (source: LinkedIn).
- Founding Team: Renaud Deraison – Creator of Nessus (source: Crunchbase).
Key Features of Nessus:

- Active vulnerability scanning and detection
- Compliance checks against industry standards (e.g., PCI DSS, CIS benchmarks)
- Configuration auditing and assessment
- Web application scanning and assessment
- Exploitability assessment and reporting
- Extensive plugin library for vulnerability coverage
Pros of Using Nessus:
- Comprehensive vulnerability scanning capabilities for systems and networks
- Customizable scan policies and reporting templates
- Scalability for large-scale deployments and enterprise environments
- Integration with other security tools and platforms
- Regular updates and support from the vendor
Cons of Using Nessus:
- Commercial licensing is required for certain advanced features and functionality
- Performance impact on scanned systems and networks during resource-intensive scans
- False positives or false negatives may require manual validation and analysis
Pricing
Nessus is available in both free and commercial editions. The screenshot below provides an example of the pricing for the commercial version.
Our Review of Nessus
Nessus has established itself as a leading vulnerability scanning tool, offering robust capabilities for identifying security weaknesses.
Its comprehensive scanning features, compliance checks, and extensive plugin library make it an invaluable asset for vulnerability management.
There are certain considerations, such as licensing and performance impact. Nessus remains a reliable and effective solution for organizations seeking to enhance their security posture through vulnerability assessment.
8. Burp Suite

Burp Suite is a powerful web application security testing platform that aids in identifying and assessing vulnerabilities in web applications. It offers various tools and functionalities designed to support manual and automated testing.
Thus it is a popular choice for security researchers, penetration testers, and developers. Burp Suite provides several benefits contributing to its widespread adoption in web application security testing.
Its intuitive interface, extensive scanning capabilities, and advanced interception and manipulation features allow users to identify common vulnerabilities.
The users can easily identify SQL injection and cross-site scripting (XSS) and perform more advanced security assessments. Additionally, Burp Suite’s extensibility through plugins and scripting enables users to customize their testing workflows. Also, the users can enhance their testing methodologies.
About Burp Suite:
- Company Valuation: PortSwigger, behind Burp Suite, is privately held.
- Employee Numbers: N/A (Available information may be limited)
- Founding Team: Dafydd Stuttard – Creator of Burp Suite (source: Crunchbase)
Key Features of Burp Suite:

- Web vulnerability scanning and identification
- Intercepting and modifying HTTP/S requests and responses
- Automated and manual vulnerability verification
- Fuzzing and payload manipulation for testing input validation
- Session management and state analysis
- Extensibility through plugins and custom scripts
Pros of Using Burp Suite:
- Comprehensive web application scanning and testing capabilities
- User-friendly interface with powerful interception and manipulation features
- Extensive plugin ecosystem for customizing and enhancing testing capabilities
- Active community support and regular updates
- Detailed reporting and documentation features
Cons of Using Burp Suite:
- The steep learning curve for beginners due to its advanced features and concepts
- Performance impact on target applications during intensive scanning and testing
- Requires adequate knowledge of web application security and testing methodologies
Pricing
Burp Suite is available in both free and commercial editions. The screenshot below provides an example of the pricing for the commercial version.
Our Review of Burp Suite
Burp Suite is a comprehensive and feature-rich web application security testing platform. Its extensive scanning capabilities, interception and manipulation features, and plugin customization support make it a valuable tool for security professionals.
There is a learning curve involved and performance considerations in it. Burp Suite’s capabilities and flexibility make it a top choice for those seeking to effectively identify and mitigate web application vulnerabilities.
9. Aircrack-ng

Aircrack-ng is a set of tools used for auditing wireless networks. Primarily it is focused on Wi-Fi security. It is designed to assess the strength of wireless encryption protocols and aid in detecting vulnerabilities in wireless networks.
Aircrack-ng provides a comprehensive suite of tools for capturing packets, performing attacks, and cracking encryption keys. It offers several benefits, making it popular among security professionals and network administrators.
Its ability to analyze and capture network traffic and its advanced cracking capabilities. Thus it enables users to assess the security of wireless networks and identify potential vulnerabilities.
By leveraging Aircrack-ng’s tools, users can audit their networks or detect unauthorized access attempts on protected networks.
Key Features of Aircrack-ng:

- Packet capturing and analysis for wireless networks
- WEP and WPA/WPA2-PSK key cracking
- Deauthentication attacks and client impersonation
- Fake access point creation for network auditing
- Interactive command-line interface for fine-grained control
Pros of Using Aircrack-ng:
- Comprehensive wireless network auditing capabilities
- Support for a wide range of Wi-Fi adapters and devices
- Extensive documentation and community support
- Cross-platform compatibility (available for Windows, macOS, Linux, and more)
- Active development and updates
Cons of Using Aircrack-ng:
- Requires advanced technical knowledge and understanding of wireless protocols
- Legal and ethical considerations when auditing networks without proper authorization
- Limited effectiveness against networks with strong security measures (e.g., WPA3)
Pricing
Aircrack-ng is an open-source tool and is available for free.
Our Review of Aircrack-ng
Aircrack-ng is a powerful and widely-respected tool for auditing wireless networks. Its comprehensive suite of tools and ability to capture and analyze network traffic makes it a valuable asset for security professionals.
However, it should be used responsibly and within legal boundaries, as unauthorized usage may have legal consequences.
Overall, Aircrack-ng is an essential tool for those involved in wireless network security assessments and Wi-Fi vulnerability detection.
10. SQLmap

SQLmap is an open-source penetration testing tool designed to detect and exploit SQL injection vulnerabilities in web applications. It automates the SQL injection flaws identification and exploitation process.
Therefore it allows security professionals and ethical hackers to assess the security posture of web applications and databases.
SQLmap provides several benefits, making it a popular choice for security assessments and vulnerability testing. Its advanced detection algorithms and extensive exploitation techniques help identify and exploit SQL injection vulnerabilities.
All these can lead to unauthorized access, data leaks, or manipulation of sensitive information. By leveraging SQLmap’s capabilities, users can evaluate the resilience of web applications against SQL injection attacks and assist in their remediation.
Key Features of SQLmap:

- Automated detection and exploitation of SQL injection vulnerabilities
- Fingerprinting of the database management system (DBMS)
- Enumeration of database tables, columns, and data
- Access to the underlying file system through out-of-band techniques
- Ability to execute custom SQL queries for advanced testing
Pros of Using SQLmap:
- Streamlines the process of identifying and exploiting SQL injection vulnerabilities
- Supports numerous database management systems (DBMS)
- Customizable payloads and injection techniques for thorough testing
- Comprehensive reporting and output formats for vulnerability documentation
- Active community support and regular updates
Cons of Using SQLmap:
- Requires a good understanding of SQL injection vulnerabilities and web application security
- False positives or negatives may require manual verification
- Unauthorized usage may have legal and ethical implications
Pricing
sqlmap is an open-source tool and is available for free.
Our Review of SQLmap
SQLmap is a powerful and reliable tool for identifying and exploiting SQL injection vulnerabilities.
Its automated approach, coupled with its extensive range of features. This makes it an indispensable asset for security professionals in web application security assessments.
However, it should be used responsibly and within legal boundaries to avoid potential misuse. Overall, SQLmap is an effective tool for detecting and mitigating SQL injection vulnerabilities in web applications.
Frequently Asked Questions – FAQs
1. What Are the Best Penetration Testing Tools?
The best penetration testing tools include Kali Linux, Astra, Nmap, Wireshark, Core Impact, Metasploit, Nessus, Burp Suite, Aircrack-ng, and SQLmap.
These tools provide a range of capabilities to suit various security testing requirements.
2. Can Beginners Use Penetration Testing Tools?
Yes, beginners can use penetration testing tools. But they may require some learning and practice. Many tools offer user-friendly interfaces and extensive documentation to support users with varying levels of expertise.
3. Are Open-Source Penetration Testing Tools As Effective As Commercial Ones?
A: Open-source penetration testing tools like Kali Linux and Metasploit are highly effective and widely used.
However, commercial tools often provide additional features, support, and customization options that may benefit specific requirements.
4. Are Penetration Testing Tools Legal?
Penetration testing is legal when performed within authorized boundaries and with proper consent.
Organizations should adhere to legal and ethical standards and seek professional assistance when conducting security assessments.
5. Can Penetration Testing Tools Cause Damage to Systems?
When used responsibly and within authorized boundaries, penetration testing tools are designed to identify vulnerabilities without causing harm.
However, exercising caution and following ethical guidelines is essential to prevent unintended consequences.
Final Thought
In the rapidly evolving world of cybersecurity, penetration testing tools play a pivotal role in identifying and mitigating vulnerabilities.
The top 10 tools we explored – Kali Linux, Astra, Nmap, Wireshark, Core Impact, Metasploit, Nessus, Burp Suite, Aircrack-ng, and SQLmap. All these tools offer a range of capabilities to address diverse security testing needs.
Penetration testing should always be conducted within authorized boundaries, following legal and ethical guidelines. Whether you are an aspiring ethical hacker or a seasoned cybersecurity professional, these tools can empower you to safeguard your digital assets and protect against potential threats.
Choose the right penetration testing tools, stay updated with the latest security trends, and continually enhance your skills to ensure a robust Defense against cyber-attacks.
- 5 Best DevOps Platform and Their Detailed Guide For 2024 - December 26, 2025
- Top 10 Cross Browser Testing Tools: The Best Choices for 2024 - October 28, 2025
- 5 Best API Testing Tools: Your Ultimate Guide for 2024 - October 26, 2025