In our technologically advanced era, where digital transformations are rapidly evolving, the importance of robust cybersecurity measures cannot be overstated. As businesses and individuals become more interconnected, the potential threat surface expands, making systems more susceptible to cyberattacks.
Vulnerabilities within software can act as gateways for malicious entities, resulting in data breaches, system malfunctions, or compromised user information. It’s in this context that the significance of having the “best vulnerability scanning software” becomes evident.
Such software tools serve as the digital sentinels of our time, scouring applications and networks to detect and report potential weak points. Identifying these vulnerabilities allows organizations to take proactive measures to protect their digital assets.
In this article, we explore vulnerability scanning and its relevance in today’s digital world, as well as what makes some tools stand out.
Quick List of 5 Best Vulnerability Scanning Software
Here’s a quick look at the scanning software we picked —
- SentinelOne Singularity: Best for AI-driven threat prevention and response.
- Intruder: Best for businesses looking for a proactive vulnerability assessment tool.
- Snyk: Best for developers needing security for open-source code.
- BurpSuite: Best for security professionals focusing on web security.
- Orca Security: Best for companies looking for an agentless and deep vulnerability scanner.
Comparison Table Of the Top Vulnerability Scanning Software.
The table below provides a general comparison of some features.
Tools | Deployment Options | Scan Type | Real-time Monitoring | Integration Capabilities | Customizability | User-Friendliness | Coverage |
 | Cloud, On-Premises | Host-based | Yes | Yes | High | High | Wide (Endpoint to Cloud) |
 | Cloud | Network-based | Yes | Limited | Medium | High | Broad Network |
 | Cloud, On-Premises | Code & Dependency Scan | Yes | Wide Range | High | High | Code and Libraries |
 | On-Premises | Web Application | No | Extensive | High | Medium | Web Apps |
 | Cloud | Full Stack | Yes | Limited | Medium | High | Cloud Infrastructure |
What is the Best Vulnerability Scanning Software?
Best Vulnerability Scanning Software are tools specifically designed to identify, assess, and prioritize vulnerabilities in computer systems, apps, and networks. In the grand scheme of cybersecurity, these software play a pivotal role in bolstering an organization’s defenses against potential cyber threats.
But what is vulnerability scanning exactly? At its core, it’s a systematic examination of a system’s potential security weaknesses. These can arise from misconfigured settings, outdated software versions, or coding errors. When these vulnerabilities are identified, they can be patched or remedied before a malicious actor has the chance to exploit them.
Labeling a software as the “best” is subjective, as what might be ideal for one organization could differ for another. Typically, the best vulnerability scanning tools offer a combination of:
Comprehensive Scanning: These tools cast a wide net, ensuring that no potential vulnerability goes unnoticed, from software bugs to configuration errors.
Real-time Monitoring: With cyber threats continuously evolving, the best tools stay vigilant, offering real-time updates and scans.
User-Friendly Interface: Ease of use is crucial. An intuitive interface ensures that even those without deep technical knowledge can navigate and understand the tool’s findings.
Detailed Reporting: After a scan, a comprehensive report highlights potential threats, their severity, and recommended action steps.
How Best Vulnerability Scanning Software Can Help Your Software Development or Testing
In the intricate web of software development and testing, ensuring security is not just a bonus—it’s a necessity. The best vulnerability scanning tools serves to identify potential security pitfalls even before they become critical.
Proactive Security from the Start
From the inception of a software project, vulnerabilities can creep in. Whether it’s through third-party integrations, overlooked coding practices, or just human error, these weak points are inevitable. The best vulnerability scanner sifts through the codebase, finding these vulnerabilities, ensuring that security isn’t just an afterthought.
Enhanced Quality Assurance
For software testers, it’s not just about functionality but also security. A vulnerability scanning tool equips testers with an additional lens, providing them insights into potential security flaws that could otherwise go unnoticed until it’s too late.
Cost-Efficiency in the Long Run
Addressing vulnerabilities post-release can be costly, both in terms of finances and reputation. Proactive scanning during development reduces the risk, saving substantial costs in the long run.
Compliance and Regulatory Adherence
Many industries mandate strict cybersecurity guidelines. Employing top-tier vulnerability scanning tools aids in meeting these regulatory standards, ensuring your software remains compliant.
Empowering Developers with Knowledge
Apart from identifying vulnerabilities, these tools often provide insights and recommendations on rectifying them. This not only fixes current issues but educates developers, enhancing their coding practices for the future.
Why Best Vulnerability Scanning Software Is Important to Your Software Testing
Software testing is an elaborate process, ensuring that applications don’t just work but work securely. The inclusion of the best vulnerability scanning tools in the testing arsenal significantly amplifies the security benchmark of the software.
Rigorous Security Checks
While manual testing has its merits, the sheer complexity of modern applications requires automated tools to delve deeper. Vulnerability scanners delve into parts that might be overlooked, ensuring a comprehensive security check.
Building Trust with End-users
Ensuring software is free from vulnerabilities isn’t just a technical requirement—it’s a trust-building measure. Users entrust software with data, and knowing it’s been vetted by top-tier vulnerability scanning tools fosters confidence.
Staying Ahead of Threats
In the ever-evolving realm of cyber threats, what’s secure today might not be tomorrow. Regular scans using the best tools keep software in sync with the latest threat intelligence, pre-empting potential future vulnerabilities.
Best Vulnerability Scanning Software
Let’s take a closer look at the software —
1. SentinelOne Singularity

With SentinelOne Singularity, your digital assets are protected with robust, AI-driven protection in the ever-changing world of cybersecurity. This system is designed to ensure the safety of diverse environments, utilizing features like active EDR, automated threat hunting, and self-operating security.
This platform steps away from the traditional, reactive security measures, choosing proactively to protect systems, learning and adapting as new threats emerge. But it’s the Singularity’s Storyline technology that truly sets it apart, painting a detailed picture of the entire attack storyline.
This kind of detailed insight is a treasure trove for security teams, allowing them to pinpoint vulnerabilities precisely, reduce alert noise, and save valuable time. As a result of its ability to integrate deeply with existing infrastructure, it is a contender for the best vulnerability scanner 2023.
About SentinelOne Singularity
- Employee numbers: 1500+
- Founding team: Tomer Weingarten, Almog Cohen, and Ehud Shamir
Key Features
Some major features of SentinelOne are given below —

Automated EDR
The feature facilitates the automatic detection and response to threats, significantly reducing the response time and ensuring that no critical alerts are missed. It operates tirelessly, providing 24/7 security, hence proving to be a reliable ally in maintaining a fortified defense perimeter.
Behavioral AI
Behavioral AI is at the heart of its real-time analysis, learning, and evolving constantly to detect threats accurately. It adapts to the changing landscape of cyber threats, offering dynamic protection against new, sophisticated threats that emerge globally.
Cloud-native Architecture
The Cloud-native architecture allows for seamless integration and scalability with your existing infrastructure. It ensures that the system remains robust and resilient, capable of adapting to the changing needs and demands of a business environment.
ActiveEDR
ActiveEDR goes beyond just monitoring; it takes actionable insights to automatically resolve threats without human intervention. This feature significantly reduces the workload on IT teams, allowing them to focus on strategic initiatives rather than getting bogged down with constant alerts.
Storyline Technology
With Storyline technology, you get a visual representation of the entire threat storyline, allowing for easy and comprehensive scrutiny of threat incidents. This empowers teams to understand the full context and make informed decisions swiftly.
Pros of using SentinelOne Singularity
- Real-time threat detection and response
- Proactive AI-driven security measures
- Visual representation of threats through Storyline technology
- Automated EDR reducing the workload on IT teams
Cons of using SentinelOne Singularity
- Might be overwhelming for small businesses
- Higher price point compared to other solutions in the market
Pricing
The pricing details for SentinelOne Singularity are not publicly available, as they offer customized pricing based on individual business requirements..
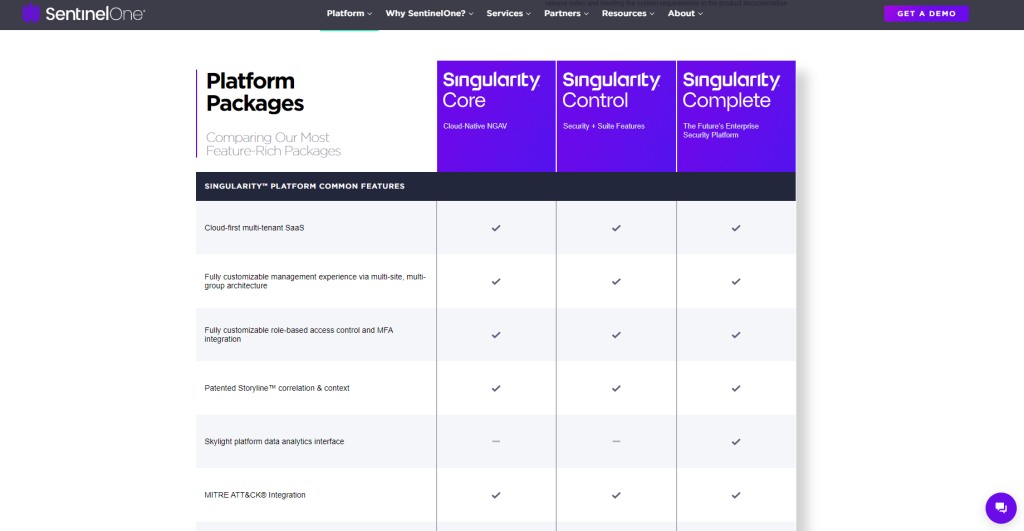
Customer Ratings
G2: 4.7 based on 153 reviews
Our Review of the SentinelOne Singularity
In a market inundated with security solutions, it clearly stands a notch above the rest, paving its path to being the potential best vulnerability scanner 2023 contender. Its AI-driven approach not only ensures real-time threat detection, but is forward-looking, learning, and evolving to protect against future threats.
The Storyline technology is like having a storyteller for your system’s security narrative, providing visual insights that are both detailed and easy to comprehend. While the price might be on the higher end, what you get is an advanced, futuristic, and autonomous security ecosystem, providing round-the-clock protection with minimal manual intervention.
The product is indeed a worthy investment for businesses looking to boost their security without drowning in alerts, bringing harmony and efficiency to the testing process.
2. Intruder
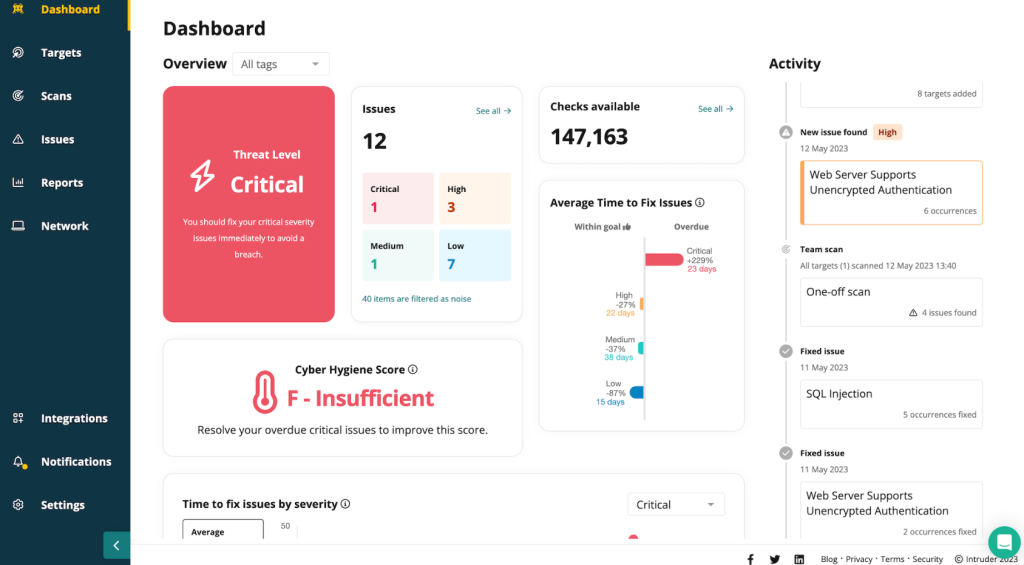
When we talk about a software that intuitively understands the vast cybersecurity landscape, Intruder makes a grand entry. Right from continuous scanning to detailed reporting, it ensures that your systems remain a fortress against potential breaches.
It is particularly noted for its user-friendly interface, making network security as straightforward as possible, sparing you from sifting through false alarms. The Intruder platform stands tall with its pre-configured scanning profiles, essentially giving you a head start in identifying and patching vulnerabilities before they can be exploited.
Moreover, it offers API access, facilitating a smooth workflow integration, which can help businesses streamline their testing process. It is also proactive in identifying vulnerabilities and providing regular updates with the latest tests, keeping your systems safe.
With Intruder, you can build resilient security postures without getting bogged down by the complexities.
About Intruder
- Employee numbers: Information not publicly available
- Founding team: Chris Wallis
Key Features
Intruder’s main features are as follows —
Continuous Scanning
Intruder’s continuous scanning feature means it diligently monitors your systems 24/7, identifying vulnerabilities as they arise. This ensures that your defense is always one step ahead, preventing potential breaches from escalating.
Over 9000 Security Checks
This feature makes sure that every nook and cranny is checked for potential security risks. It involves a battery of over 9000 checks, going through a rigorous routine to ensure that every aspect of your system is secure, hence providing a fortress-like protection to your digital assets.
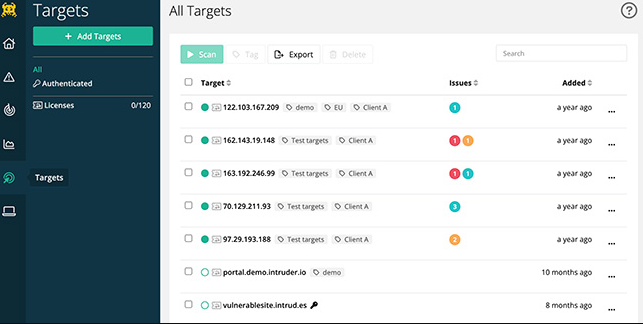
Easy to Use
Simplicity is at the core of Intruder. This feature is a boon for users who might not be tech-savvy, offering a straightforward, intuitive interface that doesn’t compromise on the depth of its security checks, essentially marrying efficiency with simplicity.
Integration with Popular Tools
Intruder offers seamless integration with popular tools like Slack, Jira, and others, facilitating a smooth workflow. It means you can have a unified workspace where security seamlessly intertwines with productivity, fostering a collaborative and secure work environment.
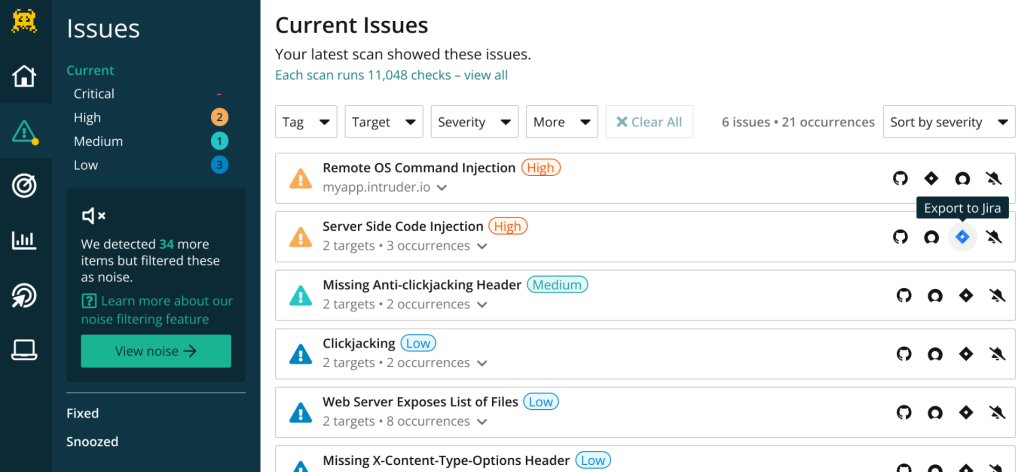
Priority Scanning
Understanding what to tackle first is vital, and this is where priority scanning comes into play. It helps in understanding how to prioritize bugs, ensuring that the most critical vulnerabilities are addressed first, thus smartly allocating resources where they are needed the most.
Pros of using Intruder
- A proactive approach to detecting vulnerabilities
- It is easy to integrate with a wide range of popular business tools
- An easy-to-use interface with a wide range of options
- Checks on the security of the system are extensive
Cons of using Intruder
- The sheer number of security checks might be overwhelming for small teams
- Lack of transparency about employee numbers could be a downside for some
Pricing
- Essential: Prices start at $113.00
- Pro: Prices start at $181.00
- Vanguard: Contact for the prices
Customer Ratings
- G2: 4.8 based on 114 reviews
Our Review of the Intruder
As we analyze Intruder, it is hard to overlook its potential as a contender for the title of the best vulnerability scanning software. The extensive battery of security checks it offers —over 9000 to be precise— speaks volumes about its thoroughness in securing your digital landscape.
What impressed us the most is the priority scanning feature. It’s like having a wise advisor, guiding you on what to focus first, a true antidote to the chaos that can sometimes engulf the cybersecurity space. Moreover, the easy integration with tools like Slack and Jira facilitates a harmonious workflow, weaving security checks seamlessly into your daily operations.
While the extensive nature of the security checks might seem a bit too much for smaller teams, larger organizations will find this depth incredibly beneficial. Intruder offers a stellar balance between depth and user-friendliness, making it a software you can trust to protect your digital assets even if you are an IT expert.
3. Snyk

With vulnerabilities often having a domino effect, Snyk appears as a beacon of resolute defense, focusing primarily on open-source libraries and other dependencies. With this solution, developers can seamlessly integrate security into existing workflows, making security an integral part of the development process.
What truly defines Snyk is its emphasis on fostering collaboration between security and development teams. This cohesive workflow ensures that security is not just a checkpoint, but a continuous journey steering alongside development projects.
This approach empowers teams to proactively address potential security issues right from the inception stage, reducing the risks significantly as the project progresses. Furthermore, Snyk offers a rich library of vulnerability data, leveraging which teams can build applications that are robust and secure by design.
As a potent tool in the developer’s toolkit, Snyk stands tall, promoting a culture of security consciousness right from the get-go.
About Snyk
- Employee numbers: 500-1000 as of the last update
- Founding team: Guy Podjarny, Danny Grander, and Assaf Hefetz
Key Features
Here are some of the main features of Snyk –

Vulnerability Detection
Snyk takes a proactive stance with its vulnerability detection feature, scouring open-source libraries and containers for any potential threats. It constantly updates its vulnerability database, which means you’re not just protected against known threats but are prepared for emerging ones as well.
Developer-First Security
This key feature is tailored to fit the needs and workflows of developers, fostering a security-conscious developer culture. It integrates effortlessly with existing developer tools and environments, creating a seamless security overlay in the development lifecycle.

Open Source Security
Given the extensive reliance on open-source components in today’s software, having a feature that specializes in open-source security is a massive boon. It offers comprehensive security monitoring and management for open-source projects, securing them from a myriad of potential vulnerabilities.

Container Security
This feature ensures that your container configurations are secure, adhering to best practices and regulatory compliances. It means not only safeguarding your applications but also ensuring they meet the necessary security benchmarks, fostering a culture of compliance and safety.

Code Security
Delving deep into the code base, this feature identifies vulnerabilities right at the source code level. It ensures that the code developed is not just functional but secure, bringing a new dimension to code quality and reliability.
Pros of using Snyk
- Developer-centric approach fostering security consciousness
- Comprehensive open-source security solutions
- Deep dive vulnerability detection in source code
- Compliance adherence in container configurations
Cons of using Snyk
- Can be resource-intensive given the depth of its scanning features
- Might come with a steep learning curve for non-developers
Pricing
- FREE – Specified Tests, No Limits for Developers
- Team – Starting at $98.00 (No Limits for Tests, 5 to 20 developers )
- Enterprise – No Limits for Tests

Customer Ratings
- G2: 4.5 based on 114 reviews
Our Review of the Snyk
Diving into Snyk’s offerings, it quickly becomes evident why it stands tall in the competitive landscape of security solutions. In addition to being a feature, its developer-first approach fosters a security-centric culture from the very beginning, which in my opinion is a breath of fresh air.
The tool does not just stop at identifying vulnerabilities; it provides actionable insights to rectify them, bringing a proactive approach to the security paradigm. This security blanket covers everything from your open-source components to the code within your digital products, despite its resource-intensive features.
Its container security ensures compliance is met without a hitch, steering clear of regulatory pitfalls. It might have a learning curve, but given the multifaceted security solutions it offers, it stands as a fortress securing your digital landscape.
For teams ready to embrace a security-centric development culture, Snyk could be the way forward, bringing robustness and reliability into your security strategy.
4. BurpSuite
Navigating the complex maze of web security is no small feat, and this is where BurpSuite becomes your trusted ally. Emerging as one of the best vulnerability scanning software, it takes a deep dive into the security landscape with a suite of tools tailored for web security testing.
It offers a rich feature set including, among others, scanning for vulnerabilities and automating tests, a true friend for penetration testers. What sets BurpSuite apart is its meticulous attention to detail; it’s not just about identifying vulnerabilities but understanding them in-depth to implement robust security measures.
Security professionals can now understand both the ‘what’ and the ‘why’ behind each vulnerability, helping them build impenetrable web applications. Additionally, teams can customize the security testing process according to individual project requirements thanks to the customizable options.
By proactively mitigating risks, BurpSuite allows you to nurture a secure, resilient web ecosystem for your business.
About Burp Suite
- Employee numbers: Information not publicly available
- Founding team: Dafydd Stuttard
Key Features
Burp Suite’s main features are –

Scanner
This feature stands as the cornerstone in Burp Suite, offering automated crawling and scanning of web applications to identify vulnerabilities precisely. It’s designed to integrate seamlessly into the testing vs debugging process, providing developers with a rich set of data to improve security postures.

Intruder
The Intruder tool in Burp Suite facilitates automated attacks on web applications, letting you find and exploit vulnerabilities effectively. It empowers users to tailor attacks to their specifics, giving a personal touch to the security processes.
Through the Intruder, you not only discover vulnerabilities, but also have a firsthand experience of exploiting them.
Repeater
Offering a simple yet potent functionality, the Repeater tool allows users to modify and resend individual HTTP/HTTPS requests, and analyze the responses from the servers. Using it, you can identify potential risks associated with your applications by dissecting every request for loopholes.

Sequencer
Burp Suite’s Sequencer tool is designed to analyze the quality of randomness in a sample of data items. Using this tool, you can find weaknesses in session management and other functionalities, ensuring a robust defense against session hijacking and other attacks.
Decoder
A tool that plays a pivotal role in security testing, the Decoder allows for the transforming of data into various formats and encodings. It means you can delve deeper, understanding how data formats work and bringing clarity to your security protocols.
Pros of using Burp Suite
- Comprehensive vulnerability scanning
- Rich set of tools for in-depth analysis
- Allows for personalized attack simulations
- Excellent for probing into session management and data randomness
Cons of using Burp Suite
- May have a steep learning curve for beginners
- Can be resource-intensive given its extensive functionalities
Pricing
- Burp Suite Professional: $449.00 1 User Per Year
- Burp Suite Enterprise Edition – PAYS: $1,999.00 Per Year
- Burp Suite Enterprise Edition: $5,999.00 Per Year
- Burp Suite Enterprise Edition – Unlimited: $49,999.00 Per Year

Customer Ratings
G2: 4.8 based on 110 reviews
Our Review of the Burp Suite
Burp Suite is undoubtedly a powerhouse in web application security, rising as a contender for the best vulnerability scanning software. Its Scanner feature stands tall, allowing for an automated yet detailed analysis of web applications, turning every stone to uncover potential vulnerabilities.
The array of tools it houses, each tailored to specific aspects of web security, brings a depth of understanding and analysis that is commendable. However, it’s not just about identifying vulnerabilities. It goes a step further, offering users the leverage to experiment with potential attacks, thereby fostering a deeper understanding and readiness against cyber threats.
While it might demand a steep learning curve, especially for beginners, it provides a robust tool that not only identifies but also helps understand potential threats. It’s more than a scanner; it’s a mentor guiding you through cybersecurity, earning its place in the top echelons of vulnerability scanner best practices and tools.
It offers a rich, detailed, and hands-on approach to cybersecurity, which is both its strength and its calling card in a highly competitive market.
5. Orca Security

Orca Security is designed to be a solution that goes beyond traditional vulnerability management. It helps to bridge the gap between security teams and the reality of modern assets. With its agentless approach, it allows for a seamless integration into any business infrastructure, identifying vulnerabilities that often slip through unnoticed.
Users are especially fond of its quick deployment. And that doesn’t require the installation of any agents on the targets, minimizing friction and maximizing efficiency. The tools it offers delve deep into the asset, giving a 360-degree view, and providing insights that are actionable, prioritized, and contextual.
This way, it ensures that businesses can move at a fast pace without compromising on security, providing a safety net that is both robust and flexible. It’s a choice for those desiring a hassle-free, yet comprehensive insight into their asset security landscape.
About Orca Security
- Employee numbers: 50-200 employees (as per the latest data)
- Founding team: Avi Shua, Gil Geron, Matan Levi, Shay Filosof, Hadas Amitay, Wagde Zabit
Key Features
Here’s what Orca Security offers —

Agentless Vulnerability Scanner
An outstanding feature of Orca Security is its agentless vulnerability scanner that revolutionizes the ease of deployment. Eliminating agents reduces the overhead of managing them, resulting in a streamlined vulnerability management solution.
In this way, businesses are provided with a hassle-free solution to maintain a stronghold on their security landscapes in a less intrusive manner.

Cloud Security Posture Management (CSPM)
CSPM is another highlight of the Orca Security suite, offering organizations an eagle-eye view of their cloud environments. Continually identifying misconfigurations, malware, and other risks, it ensures an unyielding security posture.
SideScanning Technology
Through its SideScanning technology, Orca detects vulnerabilities, malware, and misconfigurations in cloud environments without running any code. Providing a balance between efficiency and thoroughness, it ensures extensive and deep scanning.

Workload and Data Security
Ensuring that both the workload and data are secured is paramount in today’s digital landscape. Orca Security provides tools that safeguard sensitive data and maintains the workload security, giving businesses a fort-like protection.
API Integration
The API integration capability of Orca Security enables it to seamlessly weave into your existing security systems, enhancing and simplifying the workflow. It ensures that your various security solutions can work in harmony, reducing the complexity and enhancing the functionality of your security infrastructure.
Pros of using Orca Security
- Agentless approach minimizes deployment hassles
- Deep insights through SideScanning technology
- Comprehensive cloud environment overview with CSPM
- Seamless API integration with existing systems
Cons of using Orca Security
- Might require a learning curve to fully utilize all features
- Some users have noted occasional false positives
Pricing
Pricing details for Orca Security are not publicly disclosed and are provided on a case-by-case basis upon contacting the Orca Security team.

Customer Ratings
G2: 4.6 based on 122 reviews
Our Review of the Orca Security
Orca Security has indisputably positioned itself as a robust solution in the vulnerability management landscape. The product impresses with its agentless vulnerability scanner, eradicating the traditional hurdles associated with deploying agents, hence offering a streamlined approach to securing assets.
This feature, coupled with its innovative SideScanning technology, ensures that businesses can secure a deep, yet non-intrusive, insight into their security posture. Moreover, its CSPM feature stands tall, offering a diligent oversight of cloud environments, a necessity in the contemporary digital landscape characterized by robust cloud infrastructures.
The emphasis on workload and data security further amplifies its prowess, offering a fort-like protection for the most critical business assets. However, while it is power-packed with features, it might demand a steep learning curve for newcomers to fully utilize its potential.
Despite this, Orca Security largely impresses with a well-rounded offering that integrates seamlessly with existing systems, showcasing a deep understanding of the current business needs and landscape. It indeed makes a compelling case for businesses seeking a balance between comprehensive vulnerability management and operational efficiency.
Getting the Most Out of Best Vulnerability Scanning Software
Harnessing the optimal potential of the best vulnerability scanning software necessitates meticulous planning and execution. Here’s a quick guide:
- Regular Scans: Conduct scans periodically to identify and mitigate vulnerabilities timely.
- Updated Database: Ensure the vulnerability database is updated regularly to detect the latest threats.
- False Positive Handling: Be prepared to handle false positives efficiently to avoid unnecessary panic.
- Prioritize Remediations: After a scan, prioritize remediations based on the criticality of the vulnerabilities detected.
- Compliance Checks: Use the software for compliance checks to ensure adherence to security standards and regulations.
- Network Mapping: Utilize network mapping features to gain insights into the network architecture and identify weak points.
- Integration with Other Tools: Integrate with other security tools to enhance the overall security posture.
Wrapping up
As we navigated the dense forest of cybersecurity solutions, we dissected the offerings of some of the industry front-runners in vulnerability scanning. Intruder, SentinelOne Singularity, and SentinelOne Singularity each offered unique tools and functionalities.
The best vulnerability scanning software depends on your specific requirements and the landscape of your existing systems. Looking for a solution that nurtures security consciousness from the start? Snyk might be your go-to.
Perhaps you value detailed insights and a rich feature set designed for web security testing? Then, BurpSuite is your reliable companion. With SentinelOne Singularity and Intruder, security management becomes less of a chore and more intuitive, streamlined, and easy to implement.
As we wind down, our recommendation leans towards a thoughtful approach in selecting your vulnerability scanning tool. Identify the strengths of each solution, align it with your business requisites, and don’t be afraid to test trial versions.
In the cybersecurity arena, staying a step ahead is not just a strategy, but a necessity. Your strongest shield could very well be making informed choices here, proactively safeguarding your fortress.
In the grand scheme of things, securing your assets is not an expense, but an investment. Choose wisely, stay secure.
Frequently Asked Questions
1. What is vulnerability scanning software used for?
Vulnerability scanning software is designed to detect, assess, and prioritize vulnerabilities in systems, applications, and networks, aiding in proactive cybersecurity measures.
2. How often should the vulnerability scanning software be used?
For optimal security, it’s recommended to conduct vulnerability scans regularly, such as weekly or after significant system updates, depending on organizational needs.
3. Can vulnerability scanning software guarantee 100% security?
While these tools significantly bolster security by identifying weak points, no software can guarantee complete protection, making a layered defense strategy essential.
- 5 Best DevOps Platform and Their Detailed Guide For 2024 - December 26, 2025
- Top 10 Cross Browser Testing Tools: The Best Choices for 2024 - October 28, 2025
- 5 Best API Testing Tools: Your Ultimate Guide for 2024 - October 26, 2025
